Privacy Breach Policy
Terms of Use
Privacy Policy
Privacy Breach Policy
Cookie Policy
Terms & Conditions: Prodoc/Cube/Assure+
Terms & Conditions: TW FreightLegend
Terms & Conditions: TW Freight
Terms & Conditions: SpeEDI Apps
Terms & Conditions: TW Tariff Tool
Terms of Trade: TW Origin
Maintenance and Support Agreement: New Zealand
Maintenance and Support Agreement: Australia
DOCUMENT CONTROL
Document Information
| Document Name | TradeWindow Privacy Breach Policy | |
| Document Filename | TradeWindow Privacy Breach Policy (Version 1.0) | |
| Document Owner | Chief Information Officer | |
| Approved by | TradeWindow Board | Date: 25 November 2020 |
| Published by | TradeWindow | |
Revision History
| Version | Date | Author | Description of changes |
| 1.0 | 25 Nov 2023 | COO | None |
Supporting Documentation / References
- Privacy Breach Response Form (V1-0)
DEFINITIONS
‘TradeWindow’ or ‘we’ refers to Trade Window Limited, its subsidiaries and affiliates.
‘TradeWindow Users’ are Directors, employees and contractors of TradeWindow, as well as any third parties who process personal information on behalf of TradeWindow.
‘Information Privacy Principles’ are the privacy principles, rules and guidelines TradeWindow adheres to when processing personal information.
‘OPC’ Office of the Privacy Commissioner
‘Privacy Act’ refers to the Privacy Act 2020 effective from 1 December 2020.
‘Personal Information’ is any information which tells us something about a specific individual. The information does not need to name the individual, as long as they are identifiable in other ways, like through their home address.
‘Privacy Breach’ is an event where personal information is either inappropriately: disclosed, altered, lost, or accessed. Loss includes either the destruction of information or the temporary inability to access information.
‘TradeWindow’s Privacy Officer’ is the person responsible for all privacy related matters across TradeWindow on behalf of the leadership team, monitoring compliance, acting as the contact for the Office of the Privacy Commissioner for breach notification, complaints and other enquiries and to ensure TradeWindow complies with the provisions of the Privacy Act.
1. INTRODUCTION
Privacy breaches are bad news. Loss or misuse of personal information can cause people harm and damage TradeWindow’s reputation.
It is therefore important that all TradeWindow users understand how to identify, record the required information and report potential privacy breaches so we can respond appropriately and in a timely manner.
The following policy provides an overview of privacy breaches and the process we follow when a breach is identified.
1.1 What is a privacy breach?
A ‘Privacy Breach’ occurs when personal information is either inappropriately: disclosed, altered, lost, or accessed. Loss includes either the destruction of information or the temporary inability to access information.
The following expands and clarifies the meaning of the key words in the definition above:
- ‘Inappropriately accessed’ or ‘unauthorised access of personal information’ occurs when personal information that TradeWindow holds is accessed by someone who is not permitted to have access. This includes unauthorised access by TradeWindow users as well as unauthorised access by an external party (such as by hacking).
For example, a TradeWindow user browses sensitive customer records without any legitimate reason, or a computer network is compromised by an external attacker resulting in personal information being accessed without authority.
- ‘Inappropriately disclosed’ or ‘unauthorised disclosure’ occurs when TradeWindow users, whether intentionally or unintentionally, make personal information accessible or visible to others outside the organisation, and releases that information from our effective control in a way that is not permitted by the Privacy Act. This includes an unauthorised disclosure of information by a TradeWindow user.
For example, a TradeWindow user accidentally publishes a confidential data file containing the personal information of one or more individuals on the internet.
- ‘Lost’ refers to the accidental or inadvertent loss of personal information held by TradeWindow, in circumstances where is it is likely to result in unauthorised access or disclosure.
An example is where a TradeWindow user leaves personal information (including hard copy documents, unsecured computer equipment, or portable storage devices containing personal information) on public transport.
1.2 Why should breaches be reported?
The longer a privacy breach goes unreported the harder it gets to resolve. It may also mean that other privacy breaches occur if the breach is due to an ongoing problem with a system or process.
The people affected also have a right to know that their information may have been compromised. They may then be able to take steps to minimise impact on them, like informing their bank that their account or card details have been compromised.
Understanding the cause of privacy breaches allows us to develop and implement systems and processes that are more robust to prevent future breaches and protect personal information.
1.3 Notifiable privacy breaches
New Zealand’s Privacy Act 2020 requires privacy breaches that have or may cause ‘serious harm’ to the individuals affected to be reported both to the Office of the Privacy Commissioner (OPC) and normally to the affected individuals themselves “as soon as practicable”. These types of breaches are called notifiable privacy breaches.
Without reporting privacy breaches as soon as they are identified or suspected, TradeWindow may not be able to fulfil its legal obligations under the Privacy Act 2020.
Serious harm can include:
- specific damage (such as physical injury)
- loss of a benefit (such as lost income) or
- emotional harm (such as significant humiliation, loss of dignity or hurt feelings).
Whether harm is serious harm depends on a number of unique circumstances of each breach and therefore we must consider the various factors before determining if the breach has or is likely to have caused serious harm to the affected individuals.
TradeWindow’s Privacy Officer is responsible for the assessment of harm.
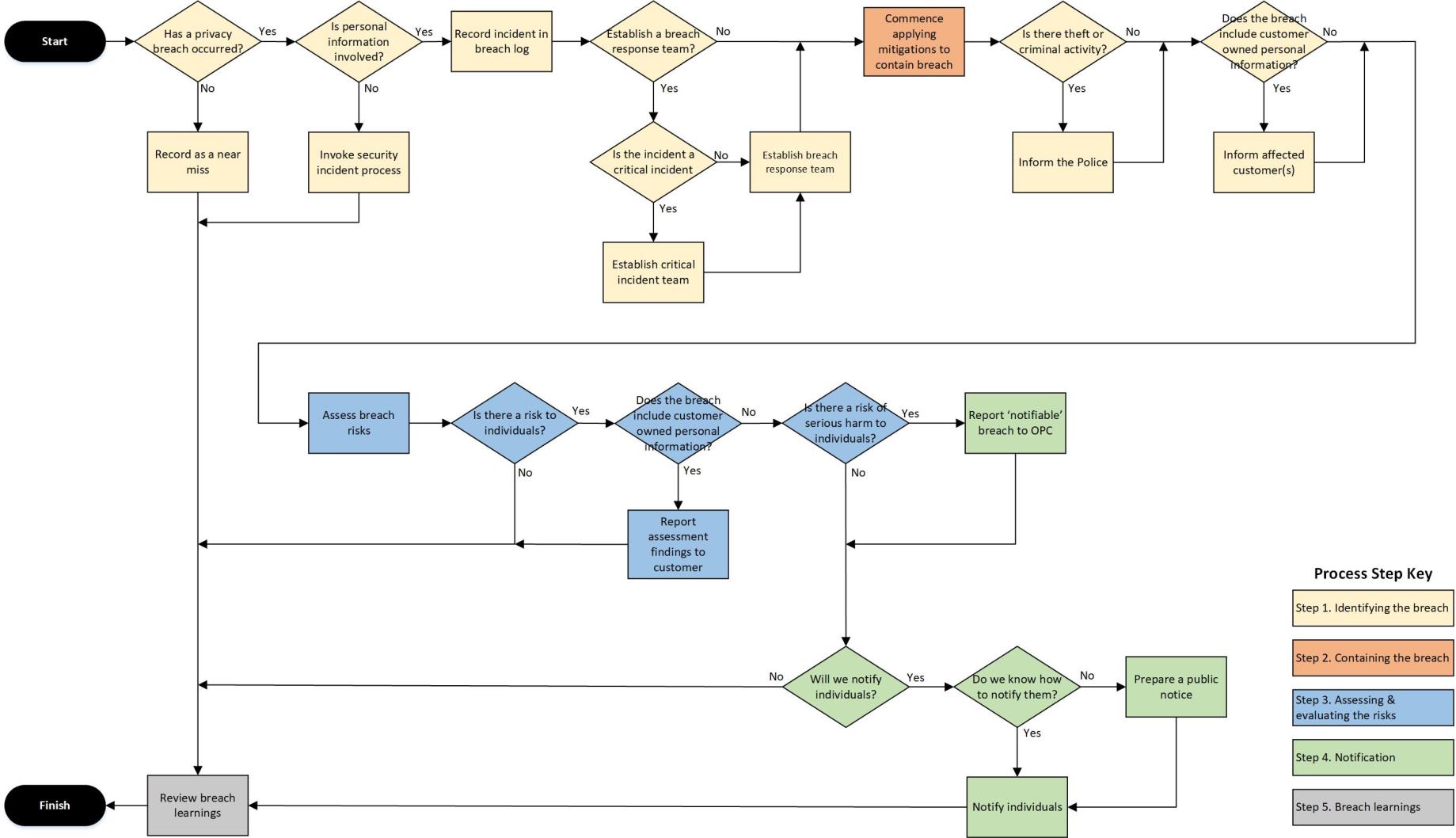
The following diagram depicts the high-level process that must be utilised for handling a privacy breach
2. HIGH-LEVEL PRIVACY BREACH PROCESS OVERVIEW
The following diagram depicts the high-level process that must be utilised for handling a privacy breach
3. PRIVACY BREACH PROCESS EXPLAINED
3.1 Purpose
The purpose of the privacy breach process is to provide a framework for TradeWindow to identify, respond and manage a privacy breach incident, or suspected privacy breach incident (known as a ‘near miss’).
The privacy breach process applies to all TradeWindow employees, contractors and third parties who process personal information for or on behalf of TradeWindow (“TradeWindow Users”).
It must be used in the event of a privacy breach, or where a privacy breach is suspected. There are five basic steps to the Privacy Breach Process:
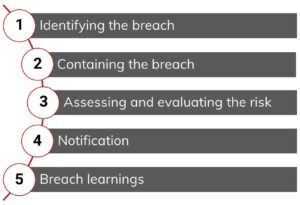
Each step is important and should not be skipped unless the process directs you to do so.
3.2 Step 1. Identifying the breach
The first step in the process is to determine if a privacy breach has occurred, how the breach has come about and if and what personal information was involved. The key is to gather enough information to then make an initial judgement call and to inform the correct people within the organisation.
Important Note. If there is no personal information involved with the breach, then the Privacy Breach Process should not be followed. Inform the Chief Information Officer, so the TradeWindow Security Incident Process can be invoked.
Privacy breaches may be identified in several ways. These could include:
- Internally from TradeWindow users
- The affected individuals themselves
- A third-party working with TradeWindow
- The Press
- The Office of the Privacy
How you deal with them and who you will need involve in the response to the breach will depend on its source.
3.2.1 Understanding if there has been a breach
As part of the identification step, you should try to determine:
- If and what personal information may have been involved?
- What was the cause of the breach?
- How was the breach discovered?
- Is the breach due to a security incident?
- Who knows about the breach?
- Who needs to know about and be involved in the breach response?
3.2.2 Reporting a breach
Any TradeWindow user, contractor or third party who discovers or is notified of a suspected or actual privacy breach must immediately report it to TradeWindow’s Privacy Officer.
3.2.3 Confirming if a breach has occurred
The Privacy Officer will work with you to confirm the details of the breach and confirm whether they believe a breach has occurred.
The Privacy Officer will also instruct you if they wish you to undertake any actions. Do not take any action unless asked to.
3.2.4 Dealing with near misses
Not all reported privacy breaches turn out to be a breach. For example it may be that you have manage to recover the information before anyone had chance to do something with it, in this scenario this would be treated as a ‘near miss’.
Near misses should still be documented and included in the Breach Log as they provide valuable information when TradeWindow is improving its security and privacy practices.
3.2.5 Logging the breach
TradeWindow maintains a log of all privacy breaches and near misses. This log must include the details of the breach, its effects and the remedial actions taken. The breach log is located in TradeWindow’s nextcloud system and it is the Privacy Officer’s responsibility to maintain this.
3.2.6 Establishing the breach response team
The TradeWindow’ Privacy Officer must be informed of all breaches. The Privacy Officer will determine whether senior management should be informed (see critical incidents below).
Once the Privacy Officer has confirmed that a breach or incident has occurred, the Privacy Officer should establish who else may need to be involved, this may include specific users, managers, and TradeWindow Information Technology team.
Important Note. If the breach includes personal information held or processed by TradeWindow on a customer’s behalf, YOU MUST inform the customer as soon as possible (see below).
Important Note. If the breach is due to a Security Incident you MUST inform the Chief Information Officer immediately.
With regards critical incidents, the Privacy Officer will gather appropriate information and in consultation with Senior Management determine whether a Critical Incident Team should be formed.
The Privacy Officer or the Senior Leadership Team may also decide that a formal investigation is required, in which case terms of reference will be established. They will also decide who else needs to be told about the incident. This may include the Board of Directors, legal advisors, and possibly insurers.
3.2.7 Informing the Police
The Police must be informed if the breach involves theft or other criminal activity.
Be careful not to destroy evidence that TradeWindow or Police might need to find the cause of the problem or fix the issue.
3.2.8 Informing customers
Where TradeWindow holds or processes personal information on behalf of its customers, we MUST notify the customer of any privacy breaches involving personal information.
Under the Privacy Act, where we are acting as a third-party or service provider, it is the customer’s responsibility to notify OPC and individuals affected in the event the privacy breach is ‘notifiable’. Therefore, it is vital we inform the customer as soon as possible after a privacy breach has been identified and confirmed.
The Privacy Officer is responsible for informing the customer.
Important Note. Some customers may have a specific process for notifying them of privacy breaches so please check how we must report a privacy breach to them.
3.3 Step 2. Containing the breach
Once a privacy breach (or suspected breach) has been identified and confirmed the first thing you must do is take steps to stop the privacy breach getting worse. As time is of the essence containment should commence even before you have established the response team or informed relevant parties.
The Privacy Officer and wider breach response team will advise on actions to be taken.
This could involve recalling an email or removing a file from a public facing website. These actions should be taken immediately to reduce the risk of harm. Containment steps could include:
- Trying to recover the lost or stolen information
- Disabling a system that may be leaking information, or has been hacked
- Stopping the practice that is causing the breach
- Changing access codes or passwords
- Identifying and fixing any weaknesses in
While containing the information, take care not to permanently delete records that will be useful to investigate the breach and any potential harm.
Note down any steps that have been taken to contain the breach in Part B: Breach Containment of the Privacy Breach Response Form and how effective you believe them to be.
Do not forget to update the breach log.
3.3.1 Communicating with customers
Where we are acting as a third-party service provider and a breach involves customer information, we need to keep the customer informed of containment actions and their effectiveness. The Privacy Officer is responsible for all communication with customers.
3.4 Step 3. Assessing and evaluating the risk
During this step of the Privacy Breach Process we need to gather the facts and evaluate the risks, including potential harm to affected individuals and the risk of the breach reoccurring.
The assessment should start as soon as containment has been achieved. Where containment involves a significant period (more than one hour) assessment can begin alongside the containment.
The Privacy Officer will assess the risks of the privacy breach to help figure out the next steps and importantly whether the breach is notifiable or not. You should consider:
- The types of personal information involved – The more sensitive the information, the higher the risk of harm to the people For example, a combination of personal information is usually more sensitive than a single piece of personal information. Health information, driver licence numbers, and credit card details can all cause harm on their own, but together they could be used for identity theft.
- What the personal information might show – For example, a list of customers on a newspaper delivery route may not be But the same information about customers who have requested that their deliveries be stopped while on holiday would be useful information to criminals.
- If the personal information is easy to access – If the information does not have a password or encryption, then there is a greater risk of someone misusing it.
- The cause of the breach – Try and find out what caused the breach and if there is a risk of further.
- The extent of the breach – Try and identify the size of the breach, including:
– How many people can access the lost information?
– How many people have lost personal information?
– The risk of the information being circulated further
– Whether the breach is the result of a systemic problem or an isolated - Who holds the information now – Information in the hands of people with unknown or malicious intentions can be of greater risk to the people The risk will be lower if you know the information went to a trusted person or organisation, and you expect them to return it.
3.4.1 Assessing ‘Serious Harm’
Whether harm is serious harm depends on all the unique circumstances of a breach.
The Privacy Officer is responsible for the assessment of harm. When considering if the privacy breach has or is likely to cause ‘serious harm’ you should consider the following:
- The nature and sensitivity of the information involved
- The number of people involved
- The degree of identifiability
- The likelihood of harm
- The potential of the information to be used for identity theft
- Any security measures used to secure the information
- The success of subsequent containment
- Any expressions by the impacted individuals
- Any potential malicious motivations of recipients of the information
- Any actions available to mitigate Serious harm can include:
- specific damage (such as physical injury)
- loss of a benefit (such as lost income), or
- emotional harm (such as significant humiliation, loss of dignity or hurt feelings).
Important Note. Harm must always be considered from the point of the people affected not from the organisation.
If the Privacy Officer determines if a breach has caused or is likely to cause ‘serious harm’ they MUST notify TradeWindow Senior Leadership Team.
Complete Part C: Assessing and evaluating the risk of the Privacy Breach Response Form is to be used in assessing the scope and size of privacy breaches and to evaluate potential harm to individuals.
Do not forget to update the breach log.
3.4.2 Communicating with customers
Where we are the third-party service provider and a breach involves customer information, we need to inform the customer of the outcome of the assessment so they can decide whether the breach has or is likely to cause serious harm and is therefore ‘notifiable’.
Important Note. We MUST NOT notify either OPC or affected individuals if we are acting as a third-party service provider.
The Privacy Officer is responsible for all communication with customers.
3.5 Step 4. Notification
Important Note. DO NOT take this step if we are acting as a third-party service provider on behalf of a customer. It is the customers responsibility to notify OPC and the affected individuals.
3.5.1 Notifiable privacy breaches
A privacy breach is ‘notifiable’ if it has caused or is likely to cause, serious harm to any individual involved in the privacy breach.
TradeWindow’s Privacy Officer is accountable for confirming on a case-by-case basis whether a breach is a notifiable privacy breach after referring to the information contained in Privacy Breach Response Form.
If the Privacy Officer believes a privacy breach may be notifiable, they must consult with the Senior Leadership Team prior to notifying anyone. They may also need to obtain legal advice and advice from other relevant parts of the business such as the Communications team.
3.5.2 Notifying the Office of the Privacy Commissioner (OPC)
TradeWindow is legally required to notify OPC of any notifiable privacy breaches as soon as reasonably practicable. All privacy breaches must be notified via OPC’s online notification tool NotifyUs.
It is important that the notification is done promptly but completely. Incomplete or ambiguous notification could cause greater harm to affected individuals.
Important Note. Ensure you have gathered all the required information (detailed below) and entered it on the Privacy Breach Response Form before lodging a breach notification within NotifyUS.
TradeWindow’s Privacy Officer is responsible for informing OPC of all notifiable privacy breaches.
3.5.2.1 NotifyUs
NotifyUs is OPC’s online tool that can help you work out if a breach is notifiable and to report it.
When reporting a privacy breach to OPC TradeWindow’s Privacy Officer may want to start by first completing the NotifyUs self-assessment, which will give you further confirmation of whether you must notify OPC of a breach. At the end of the self-assessment, you have the option to go on to complete the NotifyUs privacy breach notification report form. No information you enter in the self-assessment is sent to OPC unless you elect to go on to submit a privacy breach notification. None of the information entered is stored on the OPC website.
NotifyUs will step you through the report form with guidance at every stage and answer choices for most questions. Information required by OPC when you complete the form includes:
- Contact details: You will be asked to provide the following information about the organisation:
- Name of the organisation (TradeWindow)
- NZBN number (optional)
- Sector
- Industry classification
- You will be asked to provide information about yourself including full name, job title, email, phone number.
- Timeline: You will be asked to provide the following details about when the breach occurred:
- Is the problem that caused this breach ongoing?
- The date of the breach and the date the breach was identified by us (if different)
- About the breach: You will be asked to provide the following details about the breach:
- How many people were affected (if known)?
- The type of personal information involved in the breach
- The type of breach (i.e. what caused it)
- If you know where the information has gone, and if so, where?
- Likely harm: You will be asked to indicate how serious the privacy breach was:
- How sensitive is the information that is involved in the breach?
- Who has obtained or may obtain the information?
- What type of harm may be caused by the breach and for each type of harm you identify, what do you think the impact of the harm will be?
- How likely is it that someone will be harmed because of this breach?
- What steps have been taken to reduce the risk of harm from this breach?
- Are there security measures in place that protect the information from being accessed?
- Depending on the answers to the above questions, you might also be asked:
- Is someone’s physical safety in immediate danger?
- Is someone’s psychological safety at immediate risk?
- Is someone at immediate risk of serious financial harm?
- Notifying affected people: You will be asked about any notifications you have already made to people affected by the breach:
- Have you notified the people affected by the breach?
- If you have, you will need to state what you have done to notify the people
- If you have not, you will need to state why you have not notified the people
- If you are relying on permitted exceptions to not notify the people affected, you will need to:
- State which exceptions and why (the tool will list these exceptions for you).
- If you are delaying notifying people affected, you will need to state why, and for how long.
- If you are relying on giving public notice to notify the people affected, you will need state
- Have you notified the people affected by the breach?
- Other organisations: You will be asked about any other organisations or authorities involved:
- Were any other organisations affected by the breach, if yes, tell us who, and explain how they were affected.
- Has the breach been reported to other authorities, if yes, what authorities has the breach been reported to?
- Have you contacted any organisations (such as CERT, ID Care, Netsafe, or any other) that might be able to provide support to your organisation or people affected by the breach?
When you submit a privacy breach notification to OPC using this online NotifyUs tool, you will be issued with a unique lodgement code. You will need this code if you want to update a report previously submitted to OPC. This needs to be included in the breach log and recorded on the Privacy Breach Response form.
3.5.3 Notifying individuals
Where a privacy breach is ‘notifiable we must also notify the individuals affected. In notifying affected individuals we must consider:
- Should affected individuals be notified, if no, why?
- If affected individuals are to be notified:
- How do we notify them?
- When should we notify them?
- Who will notify them?
- What should we include in the notification? The notification to the individual must include:
- A description of the breach
- The steps we plan to take regarding the breach
- The steps an individual could take to mitigate or avoid potential loss or harm
- Confirmation that the OPC has been notified
- That the individual has the right to make a compliant to the OPC
- Contact details for the Privacy
Complete Part D: Notification, Notifying Individuals within the Privacy Breach Response Form with the details required to notify individuals.
3.5.3.1 Public notices
Where we are unable to contact affected individuals, we still have an obligation to attempt to contact them by other means, typically this involves issuing some form of public notice.
If we intend issuing a public notice we need to consider:
- What the public notice will contain?
- What form is the public notice going to take?
- When are we going to issue the notice?
- What TradeWindow contact details will be included with the notice?
Complete Part D: Notification, Notifying Individuals within the Privacy Breach Response Form with the details required to be able to issue a public notice.
3.5.4 Voluntary notification
A privacy breach does not need to be ‘notifiable’ for the Privacy Officer to decide that it is best for the affected individuals to be informed. This is also a case-by-case decision based on the relevant benefit of contacting people against any harm notifying people could cause. For example, if people are going to learn of the breach in any instance then it is best that notice of the breach comes from us directly.
3.6 Step 5. Breach learnings
Privacy breaches provide a learning opportunity. It is important that we review all privacy breaches for any important lessons. This activity will be led by whoever is delegated by the Privacy Officer.
Complete Part E: Breach Learnings of the Privacy Breach Response Form with any learnings from the breach that can be used to better prevent future privacy breaches.
It is therefore important that all privacy breaches are recorded in the breach log and the Privacy Breach Response Form attached.
4. Other Matters
4.1 Managing breaches from third parties
Should a breach involve a supplier or third-party holding information on behalf of TradeWindow then the same privacy breach process should be followed as per any other breach. The contractual relationship with the supplier or third party may include provisions requiring them to assist TradeWindow, so these should be reviewed.
4.2 Managing the media
There may sometimes be media interest in a privacy breach. If you receive a request from the media, then the breach must be immediately escalated to the Senior Leadership Team.
A response must be formulated in coordination with the Senior Leadership Team. A single spokesperson should be appointed to ensure consistency of messaging.
TradeWindow response must demonstrate empathy for any people affected by a privacy breach.